Security Override Requests
Security and User Permissions are an important part of any business software. There are occasional situations when you want to grant temporary access to something a user normally cannot access. That’s where Security Override Requests come in.
WAIT! You need to make sure Group Security is set up and active before using this feature.
Security Override Requests are based on Group Security permissions. Challenges are based on a specific user locking an area of LOU. While both require a request for access and an approval or denial of the request, they serve different purposes.
Security Override Requests grant or deny a user permission to access a feature of LOU whereas Challenges grant or deny a user control over a specific field or area of LOU for a feature they already have permission to access.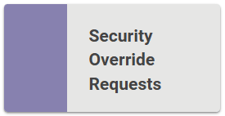
Go to Product Setup / Foundation / Security Override Requests 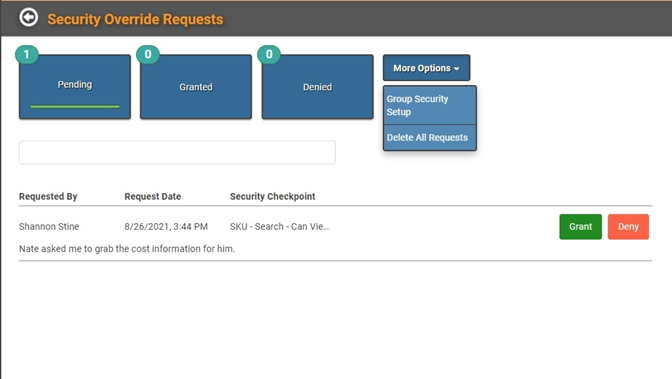
This page defaults to the Pending Security Override Requests. The Granted and Denied pages allow you to review a history of previously granted or denied requests. These pages can serve as an audit log of who requested permission, the date the request was made, what checkpoint they requested, who granted/denied permission, and when the decision was made.
IMPORTANT! Requests remain in Pending for 24 hours. After that, they are removed/expired and the user will have to make a new request.
You can use the More Options dropdown to quickly jump over to Group Security Setup or to Delete All Requests. Deleted requests cannot be recovered. Deleting requests permanently removes them from LOU. Use this option with extreme caution.
When there are pending Security Override Requests, you can click the Approve or Deny button to immediately grant or deny access to the requested checkpoint. This will send a banner alert message to the user who made the request, letting them know they have access to the checkpoint or were denied access to the checkpoint.
If you grant access to a checkpoint, that user has access to the checkpoint for 60 minutes. This access is for the entire checkpoint, not just the specific data on which they made the request.
For example, if a user requests permission to update a POS Station, they will be able to update all POS Stations for 60 minutes, not just the specific station on which they made the request.
Admin Alerts
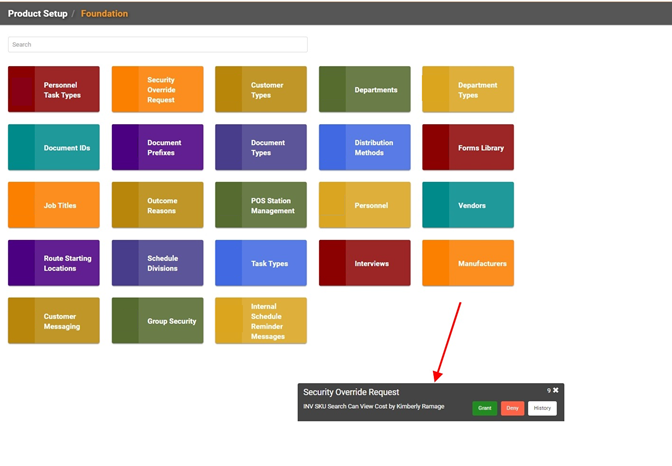
All Admins who have a phone number on their Personnel Profile will receive a text message when a request for access is made. Admins who are signed into LOU will also see a banner appear at the bottom of the screen, letting them know the request was made and giving them the chance to approve or deny it without leaving their current screen.
User Alerts
Once an Admin has reviewed the request, and made a decision, the User who made the request will see a banner with the decision on the bottom of their LOU screen. 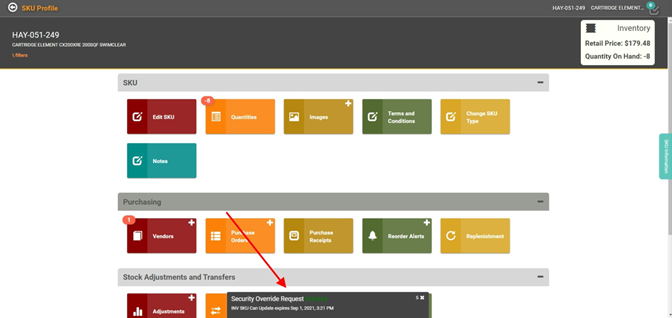
The banner will include information on what Checkpoint was granted and when the temporary access will expire.
IMPORTANT! The User will not only have access to the granted feature for the specific record on which they requested access. The User will have access to the granted feature for all records during the 60 minute approval window.
